CIGAR 'Smokes Out' Attacks on Solar Electrical Power Equipment
June 7, 2021
Contact: cscomms@lbl.gov

Rooftop solar installation in Broward County, FL. (Photo by Paul Krashefski, U.S. Department of Energy)
As green energy becomes more prevalent, solar arrays are seen as among the most promising methods for generating sustainable electricity. At the same time, inverters - the “brains” of the system, converting DC power generated by the panels to AC power ingested by the grid - are also becoming smarter, adding adaptive capabilities to respond to changing conditions in the grid.
Yet, like so many other network-connected devices, solar inverters and other equipment find themselves in the vulnerable position of being connected to networks without the traditional security protections offered to PCs, servers, and network appliances. A determined attacker could access the inverters connected to these panels and, by manipulating their settings, potentially create disturbances that could cause outages or damage to certain equipment connected to the grid.
While the need for security in the power grid is clear, cybersecurity has typically been “bolted on” in a piecemeal fashion after the fact, rather than designed in from the outset; consider, for example, significant changes to the grid that have resulted from the addition of distributed energy resources (DER) such as solar and grid-attached storage. Enter the Cybersecurity via Inverter-Grid Automatic Reconfiguration (CIGAR) project, a Lawrence Berkeley National Laboratory (Berkeley Lab) effort aimed at providing security protections for emerging power systems.
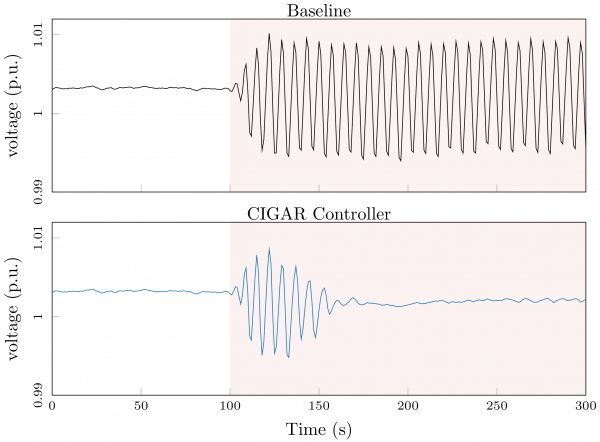
This figure depicts the voltage in a simulation of a distribution grid where a portion of smart inverters have been issued poor settings due to a cyber attack. The attacked units create a large oscillation in system voltages as depicted in the top subplot. The controller developed in the CIGAR project updates the settings in non-compromised units so that the attack is steadily mitigated (see bottom subplot). (Image: Dan Arnold, Berkeley Lab)
Lead investigators Sean Peisert and Daniel Arnold have been seeking ways to protect the grid from disturbances caused by remote attacks against rooftop solar inverters by examining everything from possible threat scenarios to defense methods and even the problems that could be caused by those protections.
“The whole purpose of these devices is energy efficiency and automation; the resources are more optimized,” said Peisert. “It opens them up to vulnerabilities.”
A Long Tradition Continues
Berkeley Lab has been active in cybersecurity research and development for decades. Its work in cybersecurity for energy delivery systems is more recent and began following the high-profile 2010 Stuxnet operation. Since then, the Berkeley Lab team has been working on a variety of projects to enhance cybersecurity for energy delivery systems. Until now, those projects have primarily focused on detecting and mitigating attacks against “traditional” power grid substation equipment. CIGAR is its first project focused on cybersecurity for distributed energy resources and was specifically designed to guard against attacks against the inverters controlling the outputs from solar arrays - attacks that could lead to potentially catastrophic grid disturbances.
The crux of the problem, according to Arnold, is that solar energy security is such an unknown field, and the responsibility for it is truly a gray area.
“There is a gap in jurisdiction in who is going to be coordinating the behavior of all of these brand new devices,” he explained.
These challenges led to the creation of CIGAR, with funding support from DOE’s Cybersecurity for Energy Delivery Systems (CEDS) R&D program. In addition to Berkeley Lab scientists, the highly multi-disciplinary and multi-institution team included a team from Arizona State University (ASU) led by Anna Scalgione, a professor of Electrical, Computer, and Energy Engineering; and teams from industry partners the National Rural Electric Cooperative Association (NRECA), led by David Pinney, and Siemens, led by Dmitriy Fradkin and Sindhu Suresh.
The project, which was recently completed, developed methods for limiting the effects of malicious actors from creating dangerous oscillations or other potentially disastrous conditions by compromising and manipulating rooftop solar inverters.
Among the first steps was threat modeling: playing the part of an attacker looking to infiltrate an array and access the panels. This included thinking up the various ways that solar inverters and utility voltage regulation and protection systems could affect power distribution grid stability.
“The fact that these devices are remote accessible and are designed to accept these parameters means there is a vulnerability,” Arnold explained. “What would happen if a bad actor could roll out settings to these devices?”
Key to those models was the development of a virtualized “twin” network that would mimic rooftop panels and provide a way for the researchers to simulate possible attack scenarios.
“The idea is to deploy the local policies learned through a digital twin of the system that can respond to such attacks by exploiting local voltage measurements,” explained Scaglione. “The main role of ASU has been the development of the digital twin that provides the ability to generate scenarios and learn the policies online, modeling the inverters and other control equipment that is conventionally deployed on the grid, helping to generate geo-embedded traces of random solar PV generation with sub-second resolution and proving fast solvers that can speed up the training.”
Thinking Like a Defender
From there, it was time to think like a defender. The team developed the ability to simulate solar irradiance on solar panels in order to identify “normal” power generation patterns, as well as means to train algorithms that can identify the optimal smart inverter settings, using reinforcement learning techniques similar to the ones used successfully by Google to train computers to play the game “Go.” This is an extensive process that needs to be performed carefully to enable grid stability in the face of cyberattacks without introducing new weaknesses.
“You don’t want to limit the capabilities of these devices,” Arnold said. “You don’t want to throw the baby out with the bathwater.”
Finally, the project integrated the methods into the NRECA’s Open Modeling Framework (OMF), a freely available, open source software package, that utilities can use to generate optimal inverter settings, based on the reinforcement learning algorithms and the utilities’ own network models.
“This work reflects a perfect alignment of market needs and cutting-edge technologies and techniques,” Peisert said. “Solar power is essential to reducing dependence on carbon-based electrical generation sources but can create new attack targets. At the same time, reinforcement learning and computing technologies that can support the heavy computational requirements of reinforcement learning have finally come to fruition.”
The CIGAR project brought all of these approaches together through the combined expertise of all the partners, scientifically demonstrated the results in numerous peer-reviewed papers, and engineered the techniques into a useful and practical set of tools, he added. “We think this work is vital to the future secure operation of distributed energy resources such as solar.”
Though the project has ended, a related effort led by Arnold, Supervisory Parameter Adjustment for Distribution Energy Storage (SPADES), is ongoing. SPADES takes a similar approach to CIGAR but applies the technique to grid-attached storage, such as the home batteries currently produced by companies like LG and Tesla.
About Berkeley Lab
Founded in 1931 on the belief that the biggest scientific challenges are best addressed by teams, Lawrence Berkeley National Laboratory and its scientists have been recognized with 16 Nobel Prizes. Today, Berkeley Lab researchers develop sustainable energy and environmental solutions, create useful new materials, advance the frontiers of computing, and probe the mysteries of life, matter, and the universe. Scientists from around the world rely on the Lab’s facilities for their own discovery science. Berkeley Lab is a multiprogram national laboratory, managed by the University of California for the U.S. Department of Energy’s Office of Science.
DOE’s Office of Science is the single largest supporter of basic research in the physical sciences in the United States, and is working to address some of the most pressing challenges of our time. For more information, please visit energy.gov/science.









